XG Firewall
See it • Stop it • Secure it
XG Firewall removes an enormous blind spot, providing extreme visibility and insight into all your network traffic, whether it’s encrypted, evasive, or elusive. XG Firewall offers more in one appliance than any other UTM, including reporting, email, and a web application firewall. XG Firewall delivers industry-proven security against malware, ransomware, intrusions, and other threats across your entire network.
- Expose Hidden Risks: Superior visibility into risky activity, suspicious traffic, and advanced threats helps you regain control of your network.
- Stop Unknown Threats: Powerful next-gen protection technologies like deep learning and intrusion prevention keep your organization secure.
- Isolate Infected Systems: Automatic threat response instantly identifies and isolates compromised systems on your network to stop threats from spreading.
- Free, Easy-to-Use VPN Client: Sophos Connect provides an intuitive VPN connection client that’s easy to deploy and configure.
Sophos Firewall Manager (SFM), Sophos Central Firewall Manager (CFM) or Sophos Central centrally manages your Sophos XG Firewall (device). Central management allows you to configure keep-alive requests and to enable configuration and signature updates of the device through the firewall manager. Having had mixed results with the Sophos XG, and having hardware that just can't keep up with the latest updates for it, I've reverted back to the Sophos UTM9. This still plays nicely with my PIA VPN setup whereby a pfSense router is placed in front of a UTM interface to anonomise traffic however I.
Imperator: rome for mac. So I was playing with certificates on the Sophos XG the other night in the hopes to publish a PRTG server through the firewall and test out the authentication and other features but in my stupidity I decided to apply a certificate to the UTM appliance itself which was invalid. I had somehow managed to import and select the wrong certificate from my machine, which was used to authenticate me as a person against StartCom where I’d got a free SSL certificate from, and completely locked myself out of the firewall admin portal *sadface*
Certificate I’d imported into the XG
When trying to access the portal on port 4444 I was greeted with errors in Chrome, IE and Firefox relating to an invalid certificate. I tried lowering all possible security settings on the browsers to no avail and ended up conceding that I’d have to bin the XG and start from a fresh build unless I found a way back in by some miracle.

“172.16.0.2 normally uses encryption to protect your information. When Google Chrome tried to connect to 172.16.0.2 this time, the website sent back unusual and incorrect credentials. This may happen when an attacker is trying to pretend to be 172.16.0.2, or a Wi-Fi sign-in screen has interrupted the connection. Your information is still secure because Google Chrome stopped the connection before any data was exchanged.
You cannot visit 172.16.0.2 at the moment because the website sent scrambled credentials that Google Chrome cannot process. Network errors and attacks are usually temporary, so this page will probably work later.”
Errors in IE and Chrome
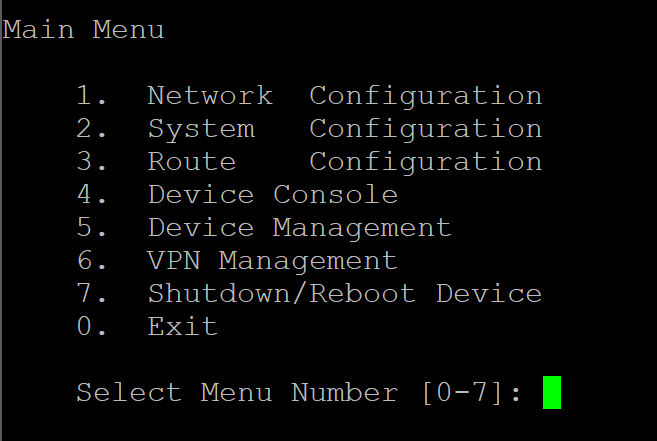
As a last ditch hope I popped a message on the Sophos community forums and within the hour I’d had a suggestion: SSH into the XG and follow the on screen prompts using options 2 and 4. This regenerated an admin portal certificate and voila, I was back in!
SSH access to the XG firewall
Prtg Sophos Xg Template
So, if you’re completely stuck with your Sophos XG, try using SSH to access it and explore the options there.
