** We will update this article with additional information as it becomes available. We have also published a playbook to guide any security team that has SolarWinds in their environment and is looking to initiate incident response. **
Rytmik lite chiptune synthesizer crack. Last updated: [2020-12-18 22:35 UTC] – view changelog
SolarWinds, an IT monitoring specialist, reported last Sunday that it had fallen victim to a “highly-sophisticated, manual supply chain attack … likely by a nation state.”
Solarwinds Sophos Software
Solarwinds MSP: Type: System tool. Try Sophos products for free Download now Download Sophos Home. Free business-grade security for the home. Endpoint Protection. Solarwinds N-Central Upload of the AMP File. Logon to Solarwinds N-Central and under Actions click on Start Automation Manager. If you already have the Automation Manager installed simply launch, if not you will need to install the Automation Manager Software.
The compromised products are SolarWinds Orion versions 2019.4 through 2020.2.1.
- The Sophos Client Firewall does not need any ports to be opened. Sophos Update Manager (SUM) SUM uses TCP port 80 for connections to an HTTP warehouse, and the NetBIOS ports for connections to a warehouse using UNC.
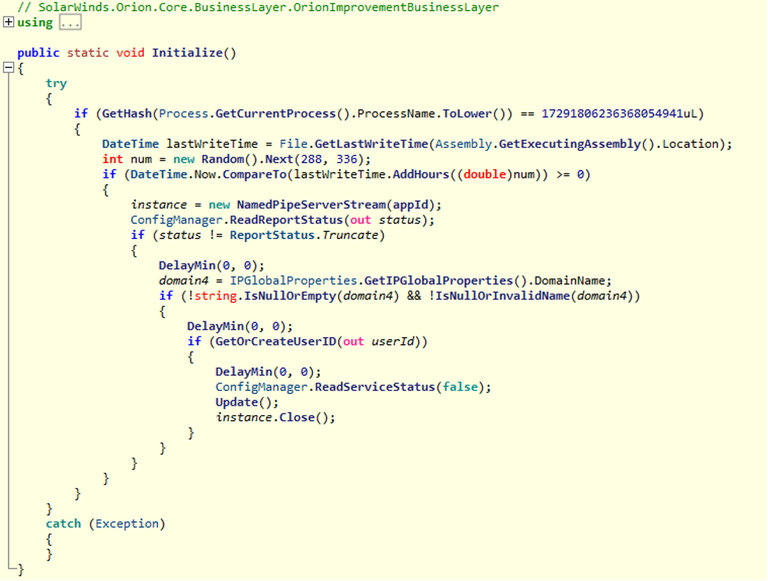
- SolarWinds and our customers were the victims of a cyberattack to our systems that inserted a vulnerability (SUNBURST) within our Orion® Platform software builds for versions 2019.4 HF 5, 2020.2 unpatched, and 2020.2 HF 1, which, if present and activated, could potentially allow an attacker to compromise the server on which the Orion products run.
How to identify if you are running an impacted SolarWinds Orion version?
Sophos customers can identify whether they are running a vulnerable version in multiple ways:
Sophos MTR customers
The MTR team is actively monitoring all protected customer environments and has already contacted affected customers directly to discuss remedial action.
Sophos EDR customers
EDR customers can run the dedicated query below to hunt for affected versions (updates will be posted here):
Additionally, EDR customers can look for the following malicious DLL SHA256 hashes:·
- 32519b85c0b422e4656de6e6c41878e95fd95026267daab4215ee59c107d6c77
- dab758bf98d9b36fa057a66cd0284737abf89857b73ca89280267ee7caf62f3b
- eb6fab5a2964c5817fb239a7a5079cabca0a00464fb3e07155f28b0a57a2c0ed
- c09040d35630d75dfef0f804f320f8b3d16a481071076918e9b236a321c1ea77
- ac1b2b89e60707a20e9eb1ca480bc3410ead40643b386d624c5d21b47c02917c
- 019085a76ba7126fff22770d71bd901c325fc68ac55aa743327984e89f4b0134
- ce77d116a074dab7a22a0fd4f2c1ab475f16eec42e1ded3c0b0aa8211fe858d6
- a25cadd48d70f6ea0c4a241d99c5241269e6faccb4054e62d16784640f8e53bc
- d3c6785e18fba3749fb785bc313cf8346182f532c59172b69adfb31b96a5d0af
- c15abaf51e78ca56c0376522d699c978217bf041a3bd3c71d09193efa5717c71
- d0d626deb3f9484e649294a8dfa814c5568f846d5aa02d4cdad5d041a29d5600
- 53f8dfc65169ccda021b72a62e0c22a4db7c4077f002fa742717d41b3c40f2c7
- 292327e5c94afa352cc5a02ca273df543f2020d0e76368ff96c84f4e90778712
- abe22cf0d78836c3ea072daeaf4c5eeaf9c29b6feb597741651979fc8fbd2417
- 2ade1ac8911ad6a23498230a5e119516db47f6e76687f804e2512cc9bcfda2b0
- db9e63337dacf0c0f1baa06145fd5f1007002c63124f99180f520ac11d551420
- 0f5d7e6dfdd62c83eb096ba193b5ae394001bac036745495674156ead6557589
Anyone not using Sophos EDR can activate a 30-day free trial and run the query across your estate:
- If you are already running Sophos Central, activate the free trial directly within your console. Under ‘MORE PRODUCTS’ in the main navigation select ‘Free Trials’ and then select Intercept X Advanced with EDR, Intercept X Advanced for Server with EDR, or both.
- If you not running Sophos Central, activate a free trial from our website.
All Sophos customers
SophosLabs has published the following anti-malware detections for the compromised SolarWinds components:
- Troj/SunBurst-A
- Troj/Agent-BGGA
- Troj/Agent-BGGB
- Troj/Agent-BGFZ
If you see one or more of these detections, you are exposed to potential attack.
Solarwinds Sophos Utm
SophosLabs has also published the following detections for the known second-stage backdoor components:
- Mal/Sunburst-B
If you see one or more of these detections, you are likely a victim of targeted attack and should take additional remediation actions.
Warning: check your configuration for scan exclusions. Seehttps://twitter.com/ffforward/status/1338785034375999491
SophosLabs is in the process of releasing IPS signatures that identify Command-and-Control traffic from the active exploitation stages of the attack. The list of IPS signatures to monitor on Sophos XG Firewall is:
- 56662 – MALWARE-CNC Win.Backdoor.Sunburst inbound connection attempt
- 56660 – MALWARE-CNC Win.Backdoor.Sunburst outbound connection attempt
- 56665 – MALWARE-CNC Win.Backdoor.Sunburst outbound connection attempt
- 56661 – MALWARE-CNC Win.Backdoor.Sunburst outbound connection attempt
If you see one or more of these IPS detections, you are likely a victim of targeted attack and should take additional remediation actions.
We have blocked all associated IP and domain indicators.
We have also revoked trust on the compromised SolarWinds certificate used in these attacks.
Sophos Application Control detects all versions of SolarWinds Orion as “SolarWinds MSP Agent”. Application Control is an optional setting – read the Help Guide for instructions on how to enable it, and add SolarWinds to the list of apps you want to block.
SophosLabs is continuing to investigate the attack and will be providing additional protection as necessary. Please monitor this location for further updates.
What do to if you are impacted
If you are running a compromised version, we recommend that you isolate the affected SolarWinds servers from the network.

We also recommend rebuilding all impacted SolarWinds servers and installing Orion Platform version 2020.2.1 HF 2 which is now available. See https://www.solarwinds.com/securityadvisory for more details.
Sophos Solarwinds Ioc
We will be releasing further incident response guidance shortly. Contact your security team or partner for advice and support where needed.
Sophos and SolarWinds
Change log
2020-12-18 22:35 UTC Updated “Sophos and SolarWinds” section
2020-12-18 16:28 UTC Updated “Sophos EDR customers” section with new malicious DLL SHA256 hashes.
2020-12-16 14:03 UTC Added Troj/SunBurst-A to anti-malware detections
2020-12-16 12:40 UTC Updated to state that Orion Platform version 2020.2.1 HF 2 is now available
2020-12-16 12:27 UTC Updated to advise that the Sophos MTR team has now contacted all affected MTR customers
2020-12-15 22:04 UTC Added Sophos detection names for second-stage backdoor components and XG IPS signatures for command and control traffic
2020-12-15 21:00 UTC Added additional Sophos detections; add an additional Hash; add signatures to monitor for
2020-12-15 12:24 UTC Added warning to check your configuration for exclusions
2020-12-15 12:06 UTC Added link to Application Control help guide, and to advise that Application Control is an optional setting that needs to be enabled.
2020-12-15 09:30 UTC Updated to add Mal/Sunburst-A to the list of Sophos detections; provide the Sophos AppControl detection; advise that we have blocked all associated IPs and domain indicators; add three further Hashes; and provide link to the playbook.
2020-12-14 18:54 UTC Updated to advise that SophosLabs has revoked trust on the compromised SolarWinds certificate used in these attacks
** We will continue to update this article with additional information as it becomes available. Check back here and GitHubregularly for further updates. **
Last updated 2020-12-15T12:18Z – view the changelog below
For security teams who have SolarWinds in their environment looking to initiate incident response, we’re providing thefollowing playbook,based upon our initial understanding of the threat,as an aid to help you investigateany potential attack.The information presented may not be complete or eliminate all threats, but we expect will be effective based on our experience. As more information becomes available about the threat, recommended steps may changeor be updated.
This response process may need to be customized for your environment and is based upon the following assumptions:
- Ability to establish when the vulnerable component was introduced into the environment and log coverage for that period.
- Assume adversaryhad access to all accounts and credentials utilized by SolarWinds Orion server and the capability to assume the identity of any administrative or related accounts.
- Assume adversaryhad the capability and network access to maintain a C2 channel to SolarWinds Orion server.
- Ability to determine that no accounts used by SolarWinds, nor accounts used to access the SolarWinds Orion server had full domain administrative rights.
- Ability to determine that no active malicious activity occurred relating to the vulnerable component based upon currently available IOCs and detections.
If you find evidence of malicious activity or if you are not able to arrive at some of the baseline conclusions described here,Sophos recommends initiatingyour full incident response procedures or reaching out for external assistance.
Hunt for impacted SolarWindsinstances
Endpointqueries
Sophos EDR/Osquery:Detection queries
Sophos Intercept X:
Sophos Application Control detects all versions of SolarWinds Orion as “SolarWinds MSP Agent”. Application Control is an optional setting – read the Help Guide for instructions on how to enable it, and add SolarWinds to the list of apps you want to block.
Labs detections: List of detections and IOCs
Manual (example):
PS C:Windowssystem32> Get-FileHash C:OrionSolarwinds.Orion.Core.Businesslayer.dll | Format-List
Algorithm: SHA256
Hash: CE77D116A074DAB7A22A0FD4F2C1AB475F16EEC42E1DED3C0B0AA8211FE858D6
Path: C:OrionSolarwinds.Orion.Core.Businesslayer.dll
Networkqueries
SolarWinds can be detected via network monitoring by looking forcall-homes made by its updating service. The following Zeek IDS searches may also help: SIEM Searches.
Note:You may only see outbound connection from your main SolarWinds instance not pollers.
Identify malicious SolarWinds components

Endpoint indicators
Warning: check your configuration for exclusions. Seehttps://twitter.com/ffforward/status/1338785034375999491
Sophos Intercept X / Central Endpoint Protection:
SophosLabs contains both detections for the malicious component and the additional signature that indicate active exploitation. Sophos has also blocked all associated IP and domain indicators for its customers. See GitHubfor detection names.
Sophos EDR/OSquery: Detection queries
Network indicators
Sophos has also blocked all associated IP and domain indicators for its XG andSG customers. If you have additional network telemetry the following searches may also be of use: SIEM Searches
Note: The attacks communicate toC2 via TLS so a file hash hit is unlikely unless you intercept TLS.
Prepare for forensics
If possible, snapshot all affected hosts with impacted versions of Orion installed.
Ensure that snapshotting processes also capture memory.
- VMware: https://docs.vmware.com/en/VMware-vSphere/6.0/com.vmware.vsphere.html.hostclient.doc/GUID-A0D8E8E7-629B-466D-A50C-38705ACA7613.html
- Hyper-V: https://support.citrix.com/article/CTX126393
A lightweight forensic acquisition can also be performed using the “Forensic snapshot” feature of Sophos EDR.
Scope potentially compromised accounts
Potentially impactedaccounts are:
- All accounts SolarWinds used for network monitoring, this includes Windows local accounts, domain accounts, SNMP, SSH, etc.
- All other accounts used on the affected SolarWinds Orion Servers. These include all administrative logins (e.g. EventCode 4624) to the server and any local or service accounts. (e.g local SQL database account.)
The following table can be used to document all potentially impacted accounts: Worms reloaded: the pre-order forts and hats dlc pack for mac.
| Username | Desc | Protocol | Domain | Domain Admin | Server admin/root | Scope | Notes |
| (fully-qualified username/UPN) | Brief overview of what it’s used by | Windows/KRB/NTLM | SNMP | SSH etc | (y/n) | (y/n) | What hosts this is applicable to |
Identify high-value attack paths for potentially compromised accounts
For all potentially compromised accounts listed above,identifyother high-value systems (e.g. domain controllers, Active Directory Federation Services, and Azure Active Directory Connect servers) to which they had access.
- Evaluate local system authentication logs for anomalous activity from compromised accounts.
- Bloodhound can also be used to map out access of any potentially impacted accounts.
If servers or accounts involved in federated authentication (e.g. ADFS servers) were potentially impacted, refer to Microsoft’s customer guidanceand develop an appropriate additional containment strategy.
Containmentand eradication
Warning: these steps assume a desire to preserve the environment for further forensic investigation and may have an impact on production environments.
- Isolate all SolarWindsOrion instances from the network:
- Instant isolation can be performed at the host level using such controls as Sophos EDR via Sophos Central.
- Host-based isolation should be backed up by network–based isolation. Systems should be migrated to an isolated non-routable VLAN with console access only (migrating to a VLAN helps preserve network state for future forensics).
- Perform credential reset or disable and recreate all potentially impacted accounts:
- Important:Ensure that no fresh or reset accounts areused to access any compromised infrastructure.
- Rebuild fresh monitoring servers from known-good sources ready for release of Orion platform version 2020.2.1 HF 2, which is planned for release on Tuesday, December 15, 2020.
- Consider taking forensic snapshots and rebuilding additional exposed hosts, including:
- Any hosts running the SolarWinds agent.
- Any hosts for which potentially compromised accounts had access rights.
Changelog
2020-12-15T12:18Z Added warning about checking your configurations for exclusions
